Blog
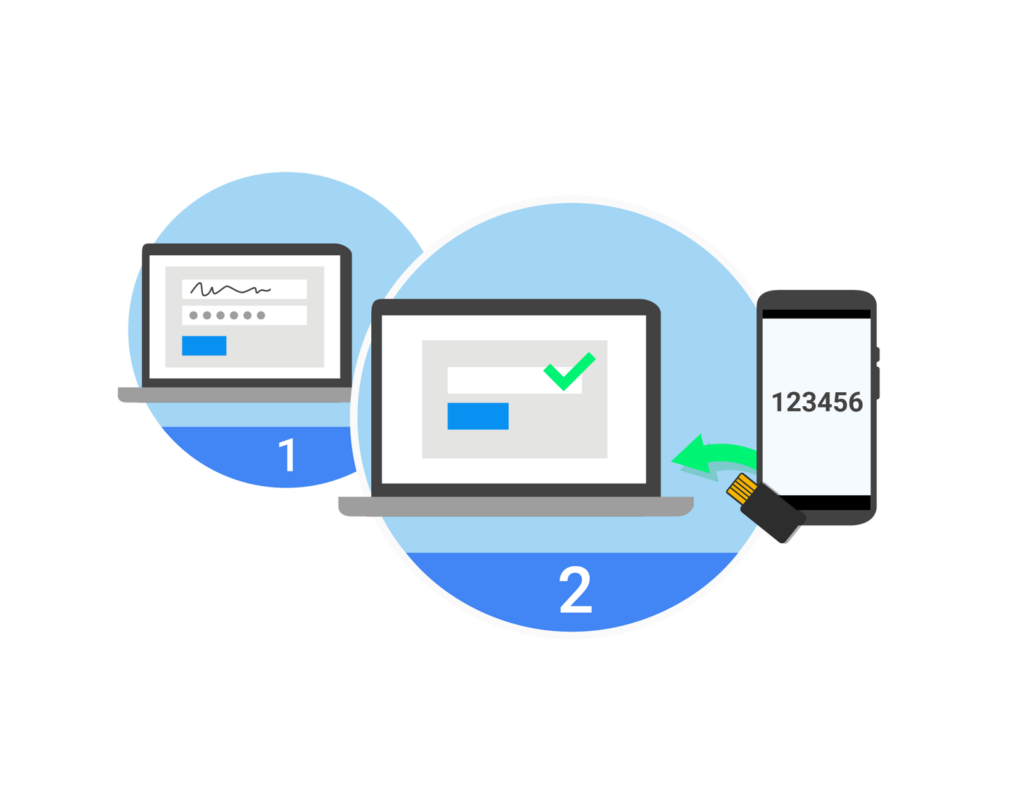
Yubikey with TecMFA
How Yubikey Enhances Multi-Factor Authentication with TecMFA As cyber attacks continue to evolve and become more sophisticated, it is...
Read More
The Importance of Desktop MFA in the Age of ChatGPT
The Importance of Desktop MFA in the Age of ChatGPT With the rise of Artificial Intelligence, the need for...
Read More
A Strong K-12 Cybersecurity Program Starts with Zero Trust
A Strong K-12 Cybersecurity Program Starts with Zero Trust In addition to providing endless learning opportunities, technology has also posed...
Read More
Technology’s Future Map
Technology’s Future Map www.credenti.io/industries The digitization of business activities has been increasing for many years. Scanning, classifying, and storing were...
Read More
The Growing Threat of Credential Stuffing: Understanding the Risks and How to Protect Yourself
The Growing Threat of Credential Stuffing: Understanding the Risks and How to Protect Yourself What is Credential Stuffing? Credential stuffing...
Read More
Exploring the Benefits and Barriers of Cloud Computing in Healthcare
Exploring the Benefits and Barriers of Cloud Computing in Healthcare What is Cloud Computing? Over the past 50 years, the...
Read More
Desktop Smart Card Authentication
For Okta users to securely access corporate resources using smart cards. Just Tap, and Go. Read More ->
Read More